They pave the way to providing autonomous vehicles with important infrastructure information in real time – whether on rail or road. Infrastructures serving the oil, gas, and water industries as well as electricity distribution networks can also become smarter if the necessary intelligence is provided locally.
Another large application field for locally networked servers are Industry 4.0 projects that implement edge analytics and where the collaborative systems copy digital twins to ensure that they can use the twin’s model to continue computations even if the network fails. It is also easy to understand why higher performing communications networks need more local computing power at the edges if bandwidths are to increase while response times are to be shortened. This impacts not only the base stations and the network nodes, but also the systems directly behind them.
Powering low-latency colocation applications – i.e., for data centres that are ‘outsourced’ to the network to enable tactile Internet applications – are ultimately shared by companies and users. In fact, these two segments account for the biggest share (54%) of the edge data centre market, which is expected to grow at a highly dynamic CAGR of 23% over the next few years, according to Global Market Insights.
Environmental conditions
Achieving this growth will often require significantly different server technology than classic IT server farms. This is because increasing decentralization means increasingly smaller edge servers will operate in increasingly harsh environments. This, in turn, requires significantly more robust systems.
Processors must be BGA mountable to ensure higher shock and vibration resistance. Ideally, they should also offer high EMI protection from electromagnetic interference to provide high operational reliability in industrial environments. The supported temperature range should also be fit for industrial use and, depending on the application, should not just extend from 0 to +60°C but also tolerate significantly hotter and colder temperatures ranging from arctic -40°C to sauna-like +85°C, which in direct sunlight can be reached quickly. Depending on the application, systems should also be able to cope with rapid temperature drops to allow opening them occasionally for servicing, even if it’s cold outside.
The maximum temperature fluctuations proposed by the ASHRAE in its edge data centre guidelines – i.e., 20°C within one hour, or 5°C max in 15 minutes – are clearly inadequate and cannot be complied with, especially when the edge data centres are smaller than a telephone booth. It must be possible to open such systems for necessary maintenance at any surrounding temperature. There isn’t even the option to quickly slip in and shut the door again for carrying out maintenance work in a closed edge server room.
Above: Secure Encrypted Virtualization, or SEV, uses AES encryption to encrypt the hypervisor and each virtual machine individually, isolating them from each other
When it’s a matter of supporting longer development cycles and operating times, which in industry can easily mean 10 years or more, the long-term availability of processor technology also plays a role. Plus, the software support industry’s needs to optimally address the specific requirements of industrial components differ from mainstream IT.
This means that IT managers, who are looking to develop edge server solutions, should opt for embedded server processor variants.
Security is essential
Under those circumstances, it is best to use rugged embedded server platforms. Sitting between cloud, office IT and operational technology (OT), they are exposed to typical IT cyber-attack scenarios and must meet highest requirements on two sides: extreme ruggedness to withstand physical stresses at the edge, and highest security requirements to thwart any hacking attempts from the Internet. What is more, edge and fog servers – like their IT counterparts in data centres – are now often designed as converged or hyper-converged infrastructures with extensive virtualization.
It is therefore not just a question of securing single systems but entire platforms, with hypervisor technology and numerous virtual machines (VMs), in order to create optimum conditions for colocation applications at the edge, or to consolidate the hardware for an overall application. When devices, machines and systems are digitized, the controllers, IoT gateways and security applications such as firewall and anomaly detection all migrate to the edge servers. The goal is to also host other devices, machines, and systems on these real-time capable servers with a view to eventually consolidating the OT of entire factories on such servers.
When factoring in the need to monetize new business models, such edge servers also become valuable vehicles to supply the required data to bill for feature-based licensing and pay-per-use services. This, of course, calls for particularly high levels of data security. Embedded server technologies from AMD offer a whole range of server security features that already take these requirements into account on the hardware side.
Hardware-based virtualization
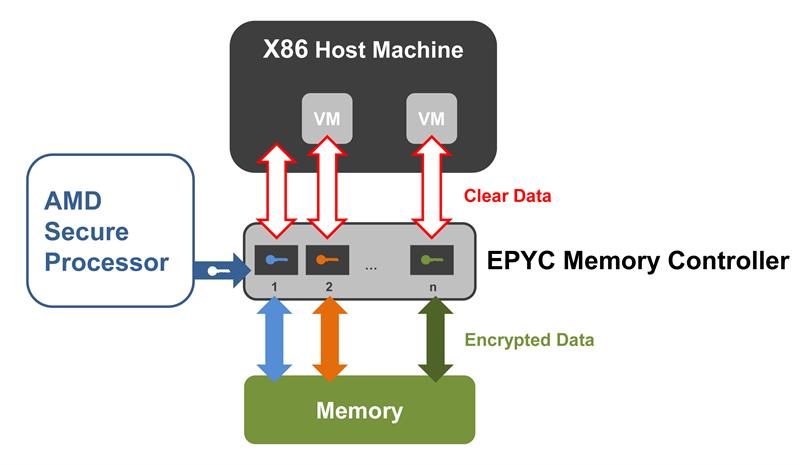
The central element and root of trust is the integrated AMD Secure Processor. It handles the security functions of the AMD Embedded EPYC processors and offers numerous 128-bit AES encrypted security features. Hence security starts with the decision to use a dedicated processor whose exclusive task it is to generate the encryption. Since this prevents the physical x86 CPU cores from accessing the encryption keys, no x86 software can monitor, extract, or modify the keys either.
Secure Encrypted Virtualization (SEV) is predestined to securely separate the heterogeneous tasks on these servers. It ensures data protection and integrity by AES encrypting each VM, thereby isolating it from the hypervisor. Each VM is assigned its own individual key, which is provided by the Secure Processor. These keys are known only to this processor, keeping data secure even if a malicious VM finds its way into the memory of another VM, or the hypervisor is compromised and infiltrates a guest VM. The AMD EPYC Embedded 7001 Series provides up to 15 individual SEV guest keys for this purpose. AMD EPYC Embedded 7002 Series processors provide as many as 509 keys.
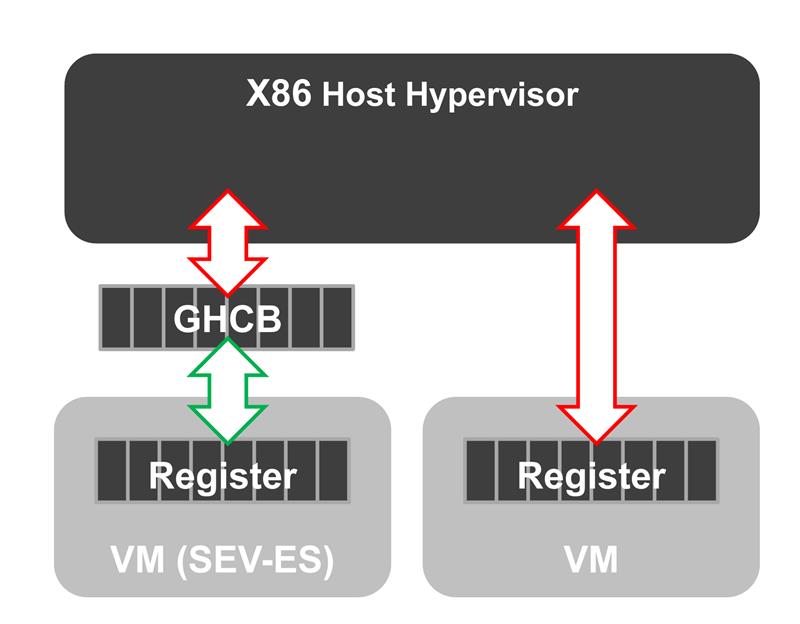
SEV Encrypted State (SEV-ES) enhances the security of the EPYC Embedded 7002 Series processors even further. Allowing the encryption of all CPU register contents after closing a VM, prevents information leakage from the CPU registers to other software components, such as the hypervisor. SEV-ES can even detect malicious modifications of CPU registers. It is important to note that unlike AMD Secure Memory Encryption, AMD SVE and SVE-ES security features require activation in the guest operating system and hypervisor. Code changes or recompilation of the actual applications, however, are not needed. So, provided the customer application runs on a system with SEV enabled, it can take full advantage of these security features.
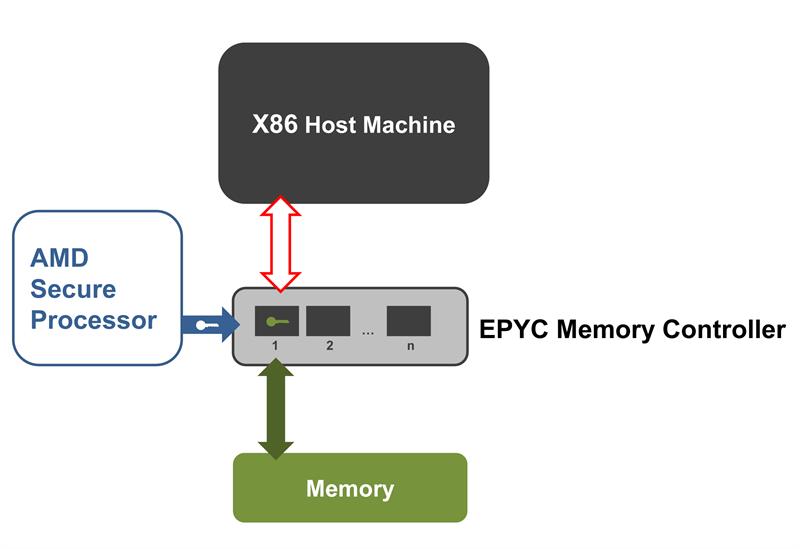
Another security element provided by the dedicated security processor is the above-mentioned Secure Memory Encryption (SME). It helps protect the integrity of the main memory, securing it against cold boot attacks or similar violations.
Attackers are unable to read the contents of the system memory in plain text even if they gain physical access to systems – which is easier to achieve in decentralized infrastructures than in secured data centres.
This encryption engine is integrated directly into the memory controller to ensure high-speed memory access. Hence the Secure Processor is a subsystem of the memory controller. Another advantage of SME is that it requires no software adaptation – neither for the hypervisor nor for the guest OS or the application software.
Author details: Zeljko Loncaric is a Marketing Engineer with congatec













